Kubernetes - Production Ops
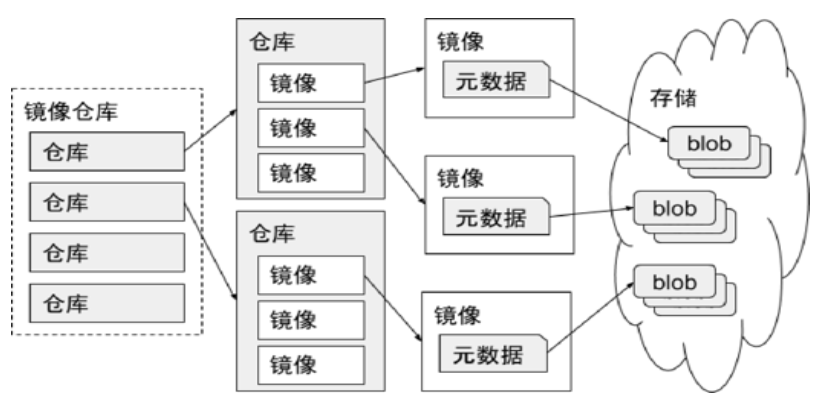
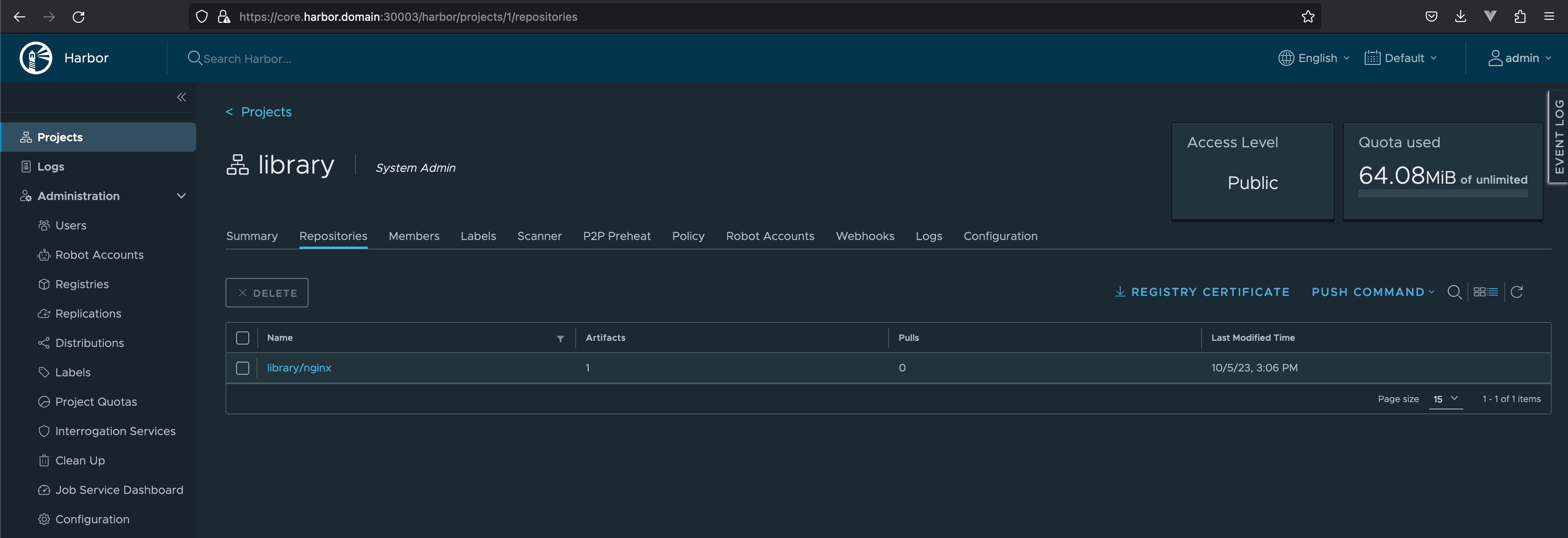
镜像仓库
- 镜像仓库(
Registry)负责存储、管理和分发镜像 Registry管理多个Repository(通过命名区分)- 每个
Repository包含一个或多个镜像(通过镜像名和标签区分) - 客户端拉取镜像:
Registry/Repository/Image:Tag
分发规范
镜像仓库应遵循
OCI Distribution Spec
| HTTP Verb | URL | Desc |
|---|---|---|
| GET | /v2/ | 检查 Registry 实现的规范和版本 |
| GET | /v2/_catalog | 获取 Repository 列表 |
| GET | /v2/ |
获取某个 Repository 下所有的标签 |
| PUT | /v2/ |
上传 Image 的 manifest 信息 |
| DELETE | /v2/ |
删除 Image |
| GET | /v2/ |
获取某个 Image 的 manifest 信息 |
| GET | /v2/ |
获取某个 Image 的文件层 |
| POST | /v2/ |
启动某个 Image 的上传 |
| PUT | /v2/ |
结束文件层上传 |
curl -s -u name:pass ${Registry}/v2/${Repository}/manifests/${Tag} | jq
1 | { |
元数据 vs 块文件
镜像由元数据(
manifests)和块文件(blobs)组成
- 元数据
- 元数据用于描述一个
镜像的核心信息- Registry / Repository / Image / Checksum / 文件层 / 镜像构建描述
- 从抽象层面完整地描述一个镜像
- 镜像是如何构建出来的
- 运行过什么构建命令
- 构建的每一个文件层的校验码
- 镜像标签
- 镜像的校验码
docker image inspect查看的是镜像的元数据信息
- 元数据用于描述一个
- 块文件
- 块文件是
组成镜像的联合文件层的实体 - 每个块文件是一个
文件层,内部包含对应文件层的变更
- 块文件是
docker image inspect nginx:1.25.2
1 | [ |
1 | $ docker history nginx:1.25.2 |
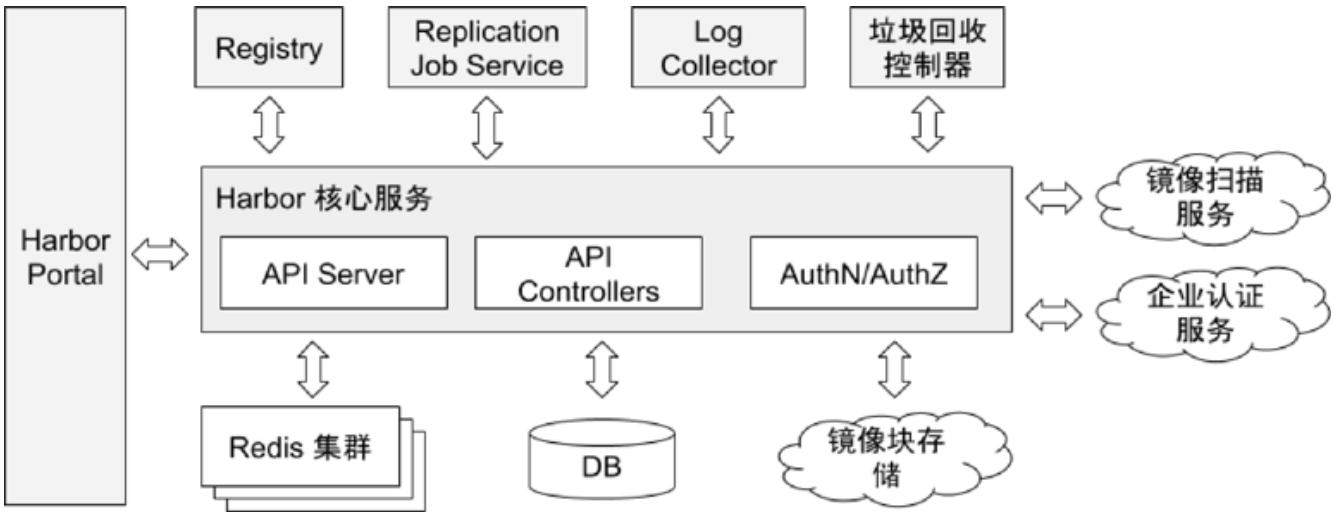
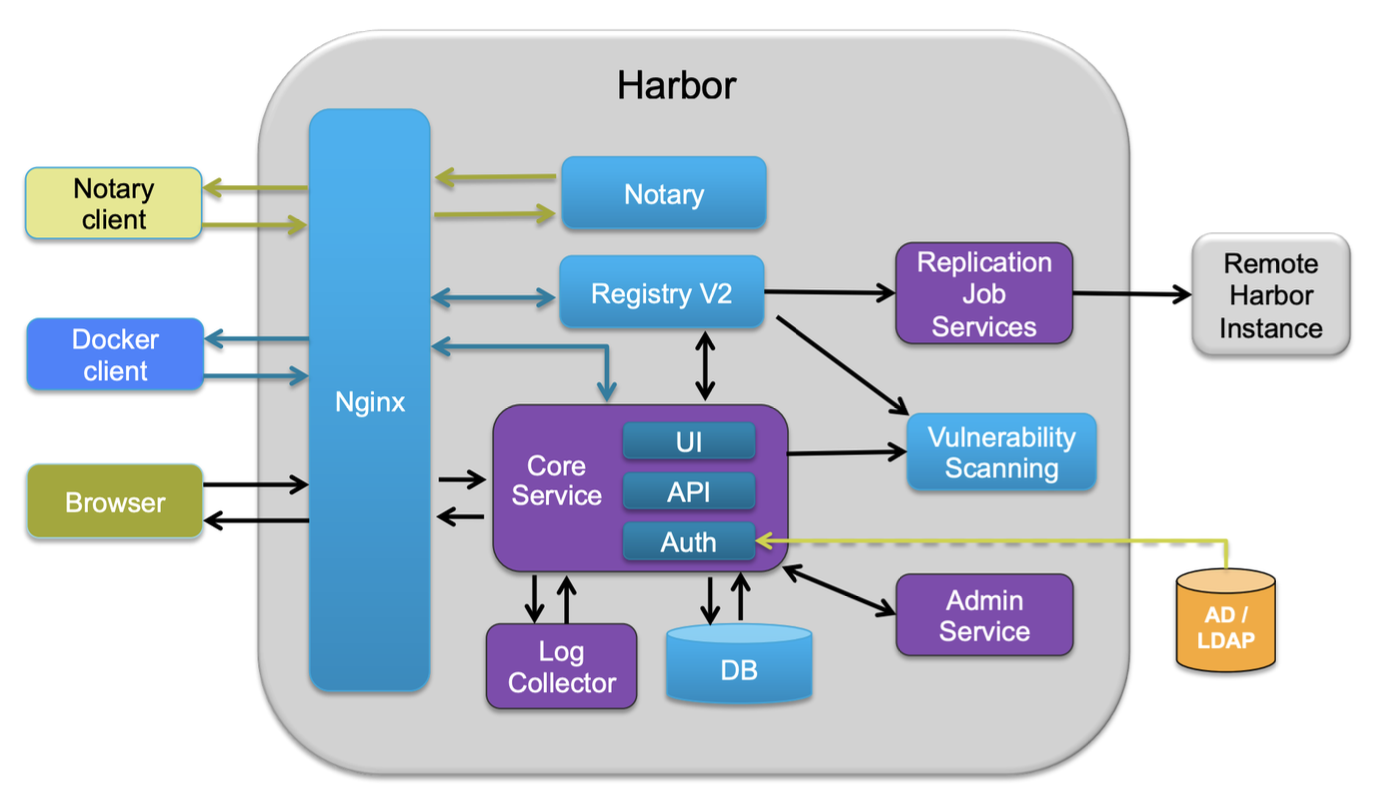
Harbor
Harbor 是 VMware 开源的企业级 Registry,已 CNCF 毕业
核心模块
| Module | Desc |
|---|---|
| Harbor Core | 仓库管理、认证管理、授权管理、配置管理、项目管理、配额管理、签名管理、副本管理等 |
| Harbor Portal | Web 界面 |
| Registry | 负责接收客户端的 Pull / Push 请求 |
| Replication Job Service | 可以以主从模式部署 Registry,将镜像从主 Registry 分发到从 Registry |
| Log Collector | 收集各模块的日志 |
| GC Controller | 回收删除镜像(默认只删除元数据)记录后遗留在块存储中的孤立块文件 |
核心架构
Helm
完成安装
1 | $ h list -n harbor |
Portal
浏览器导出 cer,通过 openssl 转换成 crt
1 | $ openssl x509 -inform PEM -in core.harbor.domain.cer -out ca.crt |
为 Docker 配置证书并重启 Docker
1 | $ sudo mkdir -p /etc/docker/certs.d/core.harbor.domain |
配置域名解析(IP 为 harbor svc vip)
1 | 10.106.237.84 core.harbor.domain |
登录
1 | $ docker login -u admin -p Harbor12345 core.harbor.domain |
为镜像打标签并推送到 Harbor
1 | $ docker tag nginx:1.25.2 core.harbor.domain/library/nginx:1.25.2 |
查询
repositories和blobs
1 | $ k exec -it -n harbor harbor-registry-869779cf47-clpll -- bash |
1 | $ k exec -it -n harbor harbor-database-0 -- bash |
HA
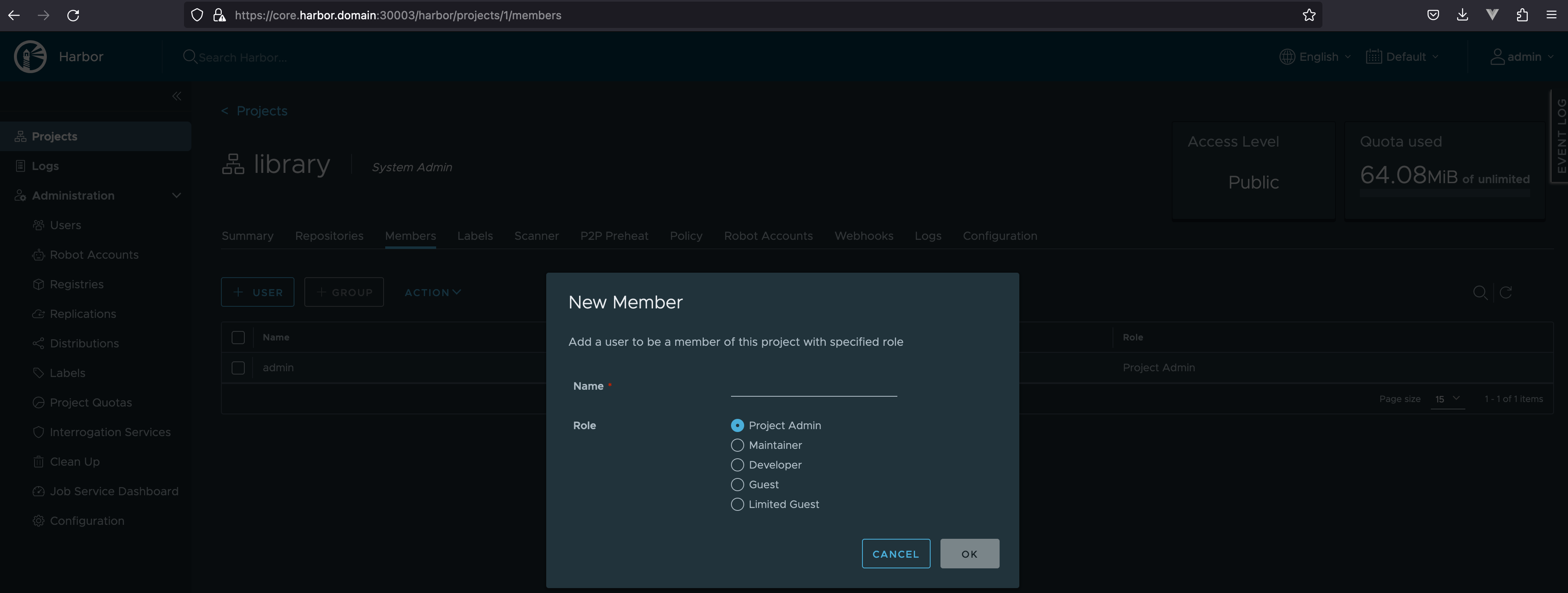
User
public 仓库可以直接 pull
| Role | ACL |
|---|---|
| Guest | docker pull |
| Developer | docker pull/push |
| Admin | all |
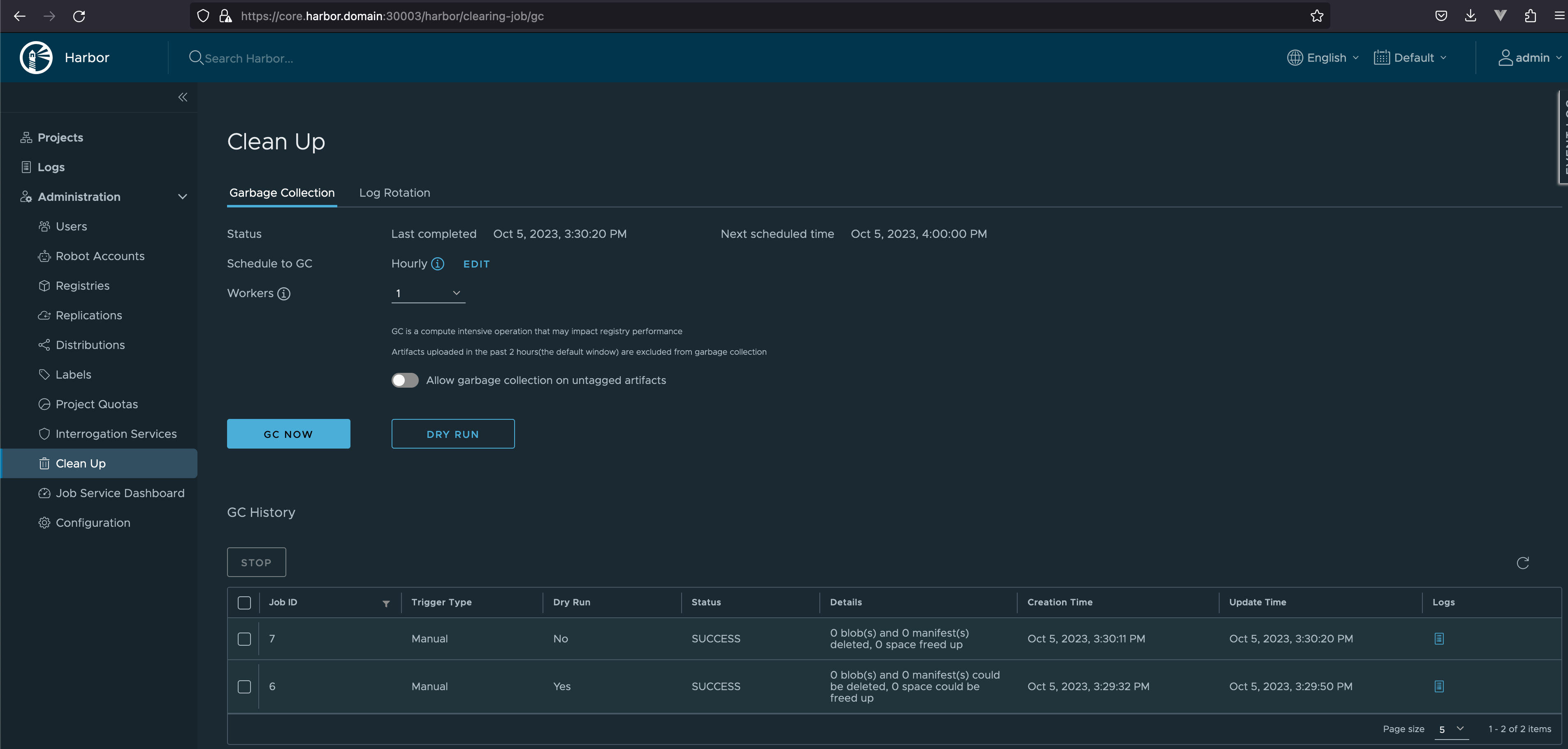
GC
镜像删除时,blob 文件不会被删除(因为分层,减少磁盘占用),需要 GC 来删除没有被引用的 blob,进而回收存储空间
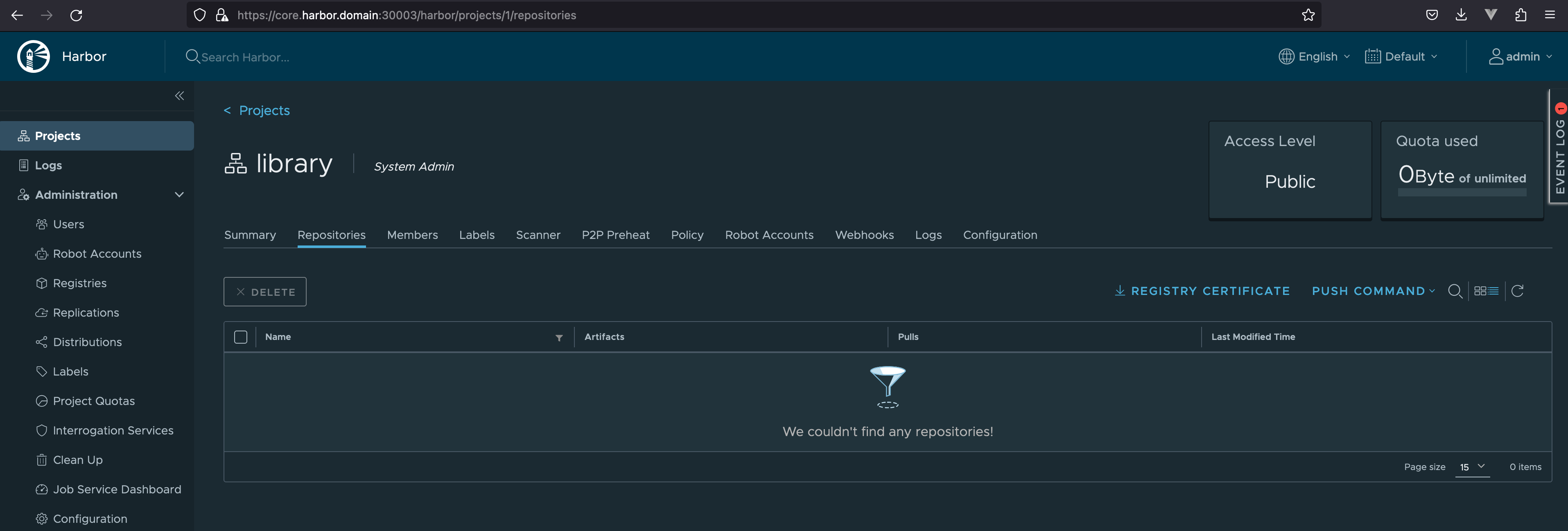
删除 core.harbor.domain/library/nginx:1.25.2
再次推送 - Layer already exists
1 | $ docker push core.harbor.domain/library/nginx:1.25.2 |
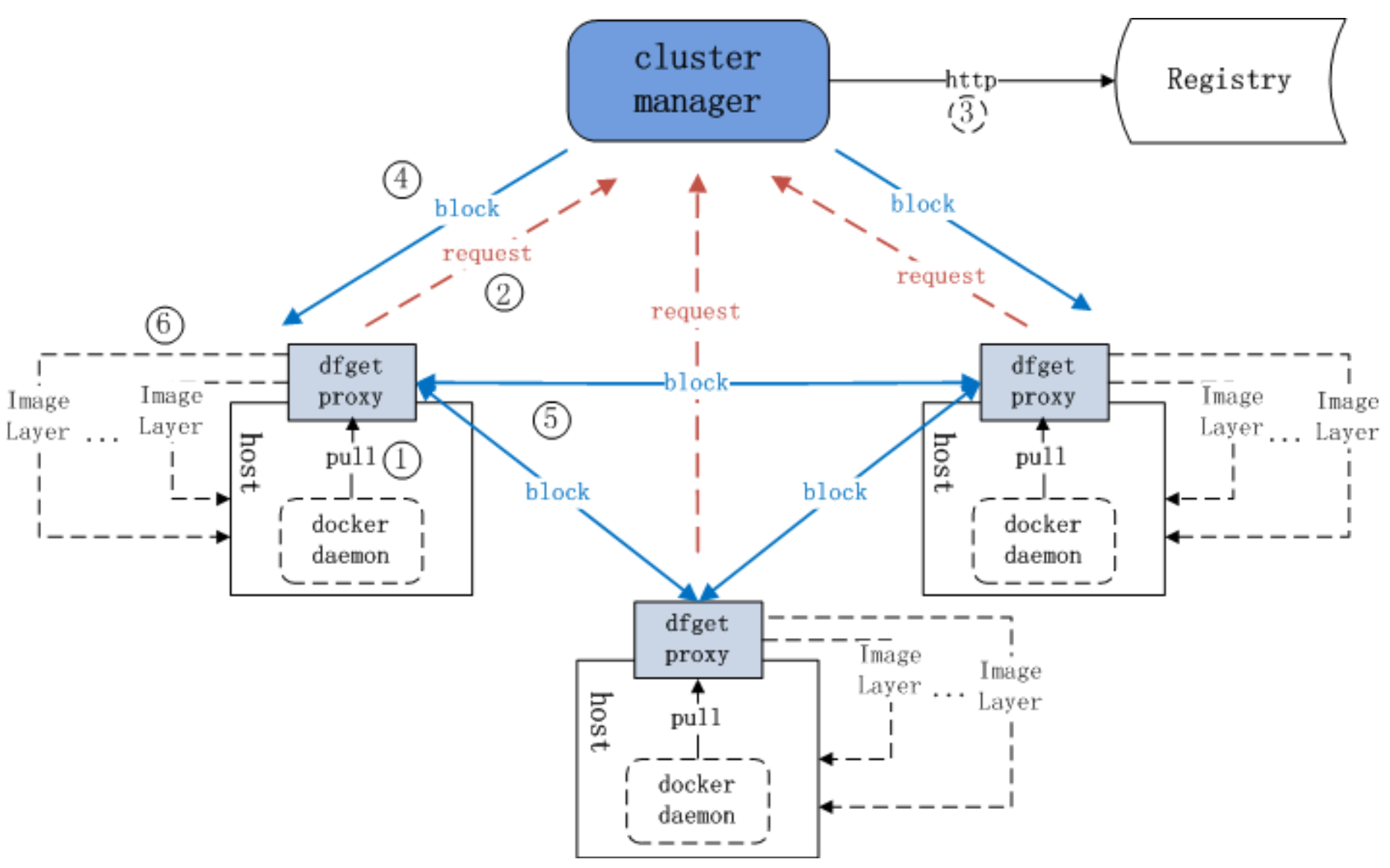
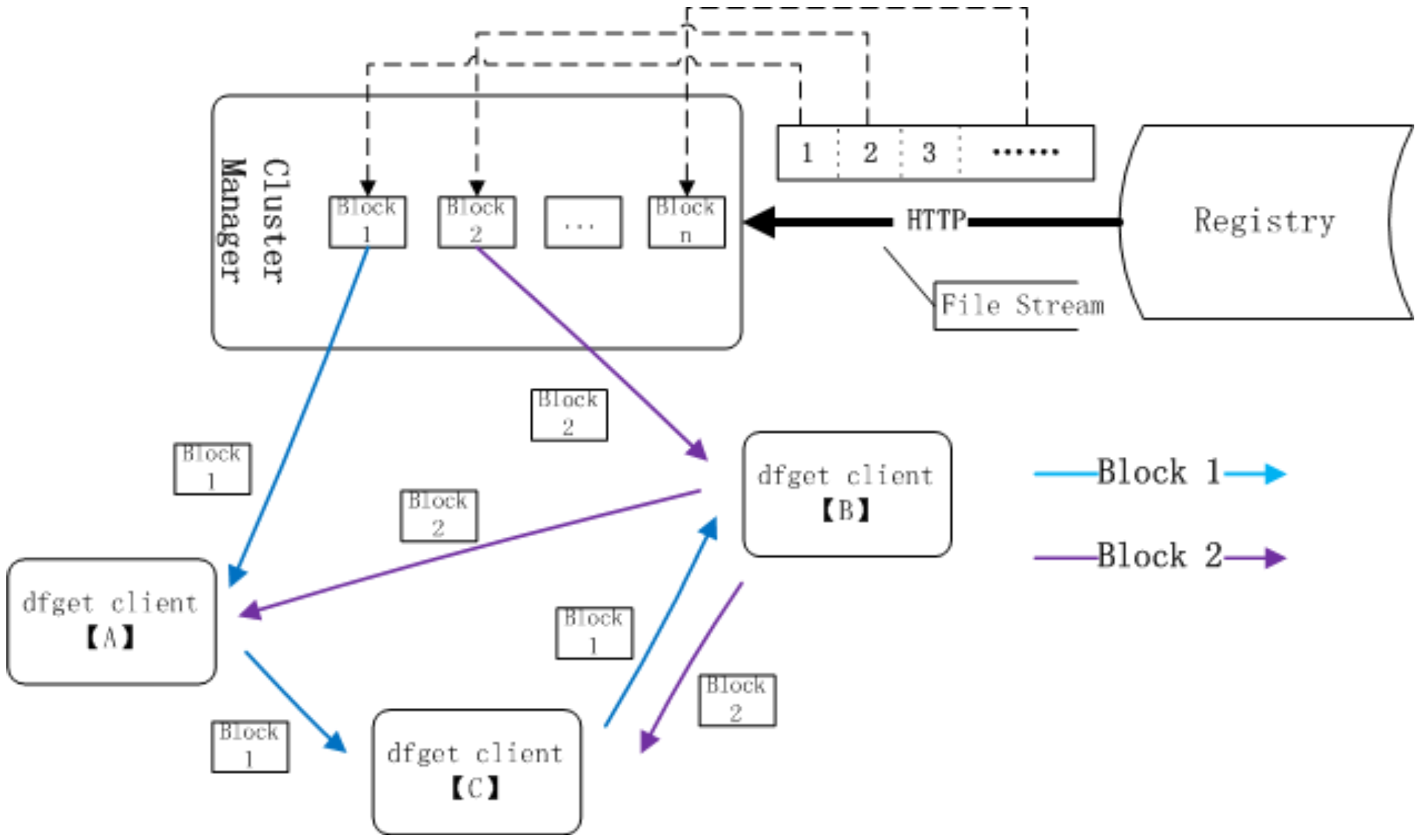
Dragonfly
基于
P2P的智能镜像和文件分发工具,提高文件传输效率,最大化利用网络带宽
非侵入性支持所有类型的容器技术
dfget proxy拦截来自于docker pull/push的 HTTP 请求,然后使用 dfget 来处理那些与镜像分层相关的请求
每个文件会被分成多个 Block,这些 Block 会在 Peer 之间传输
镜像安全
最佳实践
| Scope | Action |
|---|---|
| 构建指令 | 配置与代码分离,避免在构建镜像时添加敏感信息 |
| 应用依赖 | 避免安装不必要的依赖,确保依赖无安全风险 |
| 文件分层 | 如果敏感信息位于 lower,即便 upper 屏蔽删除(逻辑删除),依然可以获得原文件 |
镜像扫描
CVE - Common Vulnerabilities and Exposures
- 分析构建指令、应用、文件、依赖包
- 查询 CVE 库和安全策略
- 检查镜像是否安全,是否符合企业的安全标准
扫描过程 - 静态分析
- 镜像扫描服务从镜像仓库拉取镜像
解析镜像的元数据解压镜像的每一个文件层- 提取每一层所包含的依赖包、可运行程序、文件列表、扫描文件内容
- 将扫描结果与
CVE 字典、安全策略字典进行匹配,以最终确定镜像是否安全
Harbor provides
static analysis of vulnerabilities in imagesthrough the open source projectsTrivyandClair.
镜像准入
ImagePolicyWebhook admission controller
可观测性
Loki
低成本- 标签 + 压缩
借鉴了Prometheus的思想,不做全文索引
标签- 基于仅索引日志的元数据而构建的- 日志数据本身被
压缩并存储在 OSS 或者 Local FileSystem
Prometheus -> Grafana -> Grafana Loki
日志采集
| Component | Desc |
|---|---|
| Promtail | 发现采集目标以及给日志流添加上 Label 后发送给 Loki服务发现是基于 Prometheus 的服务发现机制实现的(一脉相承) |
| Loki | 可以水平扩展,支持 HA 和多租户使用与 Prometheus 相同的服务发现机制,将 Label 添加到日志流中,而不是建立全文索引Promtail 接收到的 Log 和应用的 Metrics 具有相同的 Label 集合 |
| Grafana | 一个用于监控和可视化观测的开源平台,支持非常丰富的数据源在 Loki 技术栈中,Grafana 专门用来展示来自于 Prometheus 和 Loki 的时间序列数据 |
架构
| Component | Desc |
|---|---|
| Distributor | 负责处理 Promtail 写入的日志一旦 Distributor 接收到日志数据,会将它们 分批(先聚合),然后并行地发送到多个 IngesterDistributor 与 Ingester 通过 gRpc 进行通信Distributor 是 无状态的,基于一致性哈希 |
| Ingester | Ingester 负责将日志数据写入持久化存储(S3 等)Ingester 会校验采集的日志 是否乱序(日志行是否按时间戳递增) |
| Querier | 处理 LogQL(类似于 PromQL) |
Hello Loki
1 | $ k get po |
1 | apiVersion: v1 |
1 | $ echo -n 'YWRtaW4=' | base64 -d |
Loki - Log
Prometheus - Metrics
Prometheus
Prometheus 需要较多的
内存和存储,数据是不汇聚的
Node
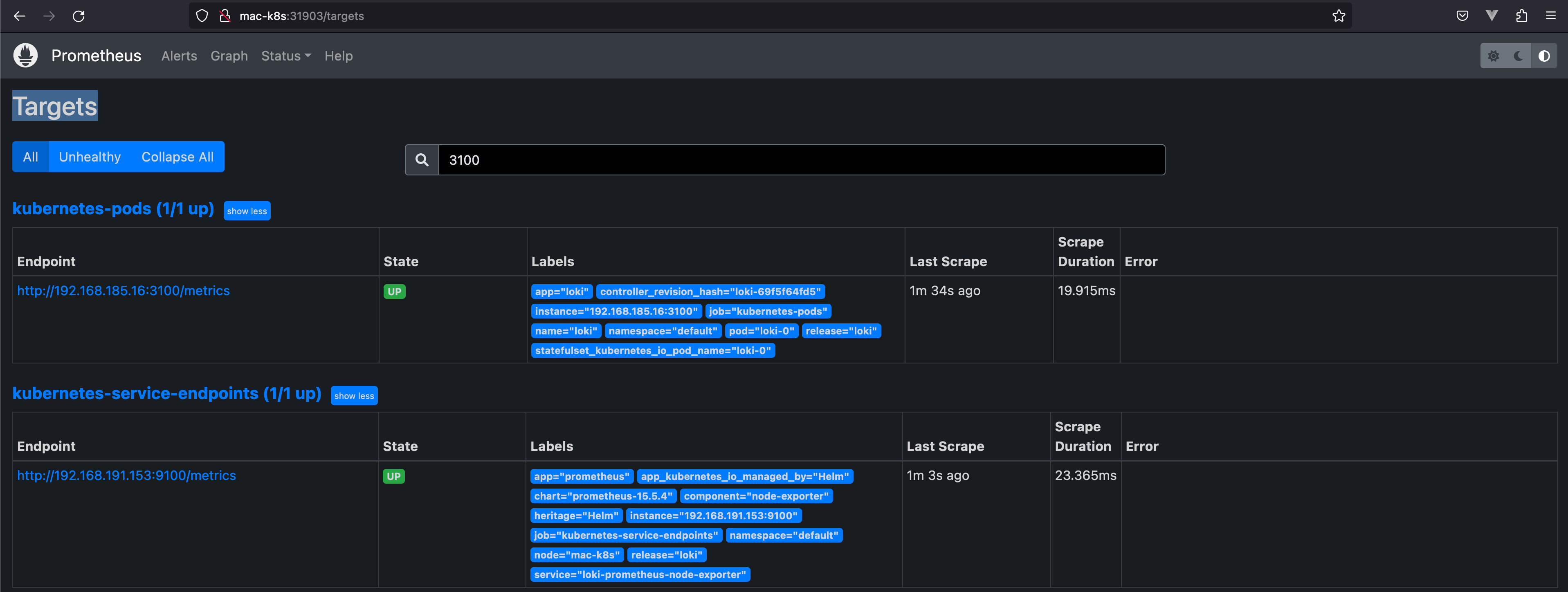
kubelet(集成cAdvisor)会收集当前 Node 上的所有信息,信息来源为CGroup,Prometheus 会拉取这些信息
Pod
Pod 通过
Annotation声明上报端口,Prometheus 会服务发现这些 Endpoint
1 | apiVersion: v1 |
App 要暴露 Prometheus Metrics
Metrics
| Type | Desc |
|---|---|
| Counter | 单调递增 |
| Guage | 可增可减 |
| Histogram | 划分 Bucket:均等 / 指数 |
| Summary | 与 Histogram 类似,但直接存储分位值,而不是通过 Bucket 计算 |